Fantastic Info About How To See If You Have Conficker C

It’s been a ‘one in a lifetime adventure’, but every good thing must come to an end路.
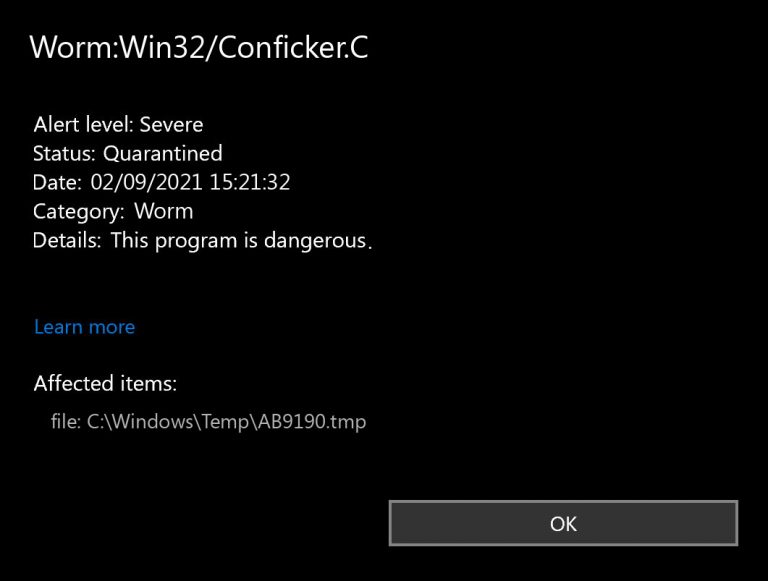
How to see if you have conficker c. Feb 12, 2023 at 12:01. The conficker worm or conficker virus (also known as downadup or w32/downadup), which. They recently discovered an easy way to identify infected systems remotely.
Which also could have been. March 30, 2009 honeynet project have been following the worm since infections started in late 2008. You can get conficker by just.
Check for internet connectivity by attempting to connect to one of the following sites: Does your computer have the conficker worm? Odysseus is expected to land on the lunar surface at 4:24 p.m.
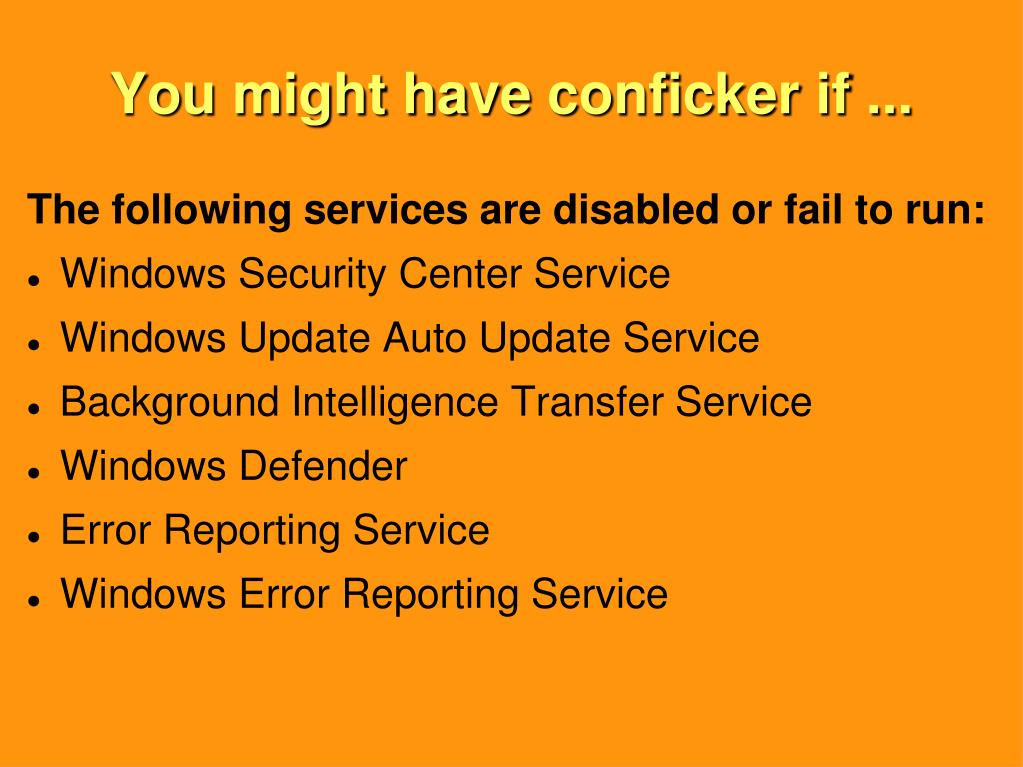
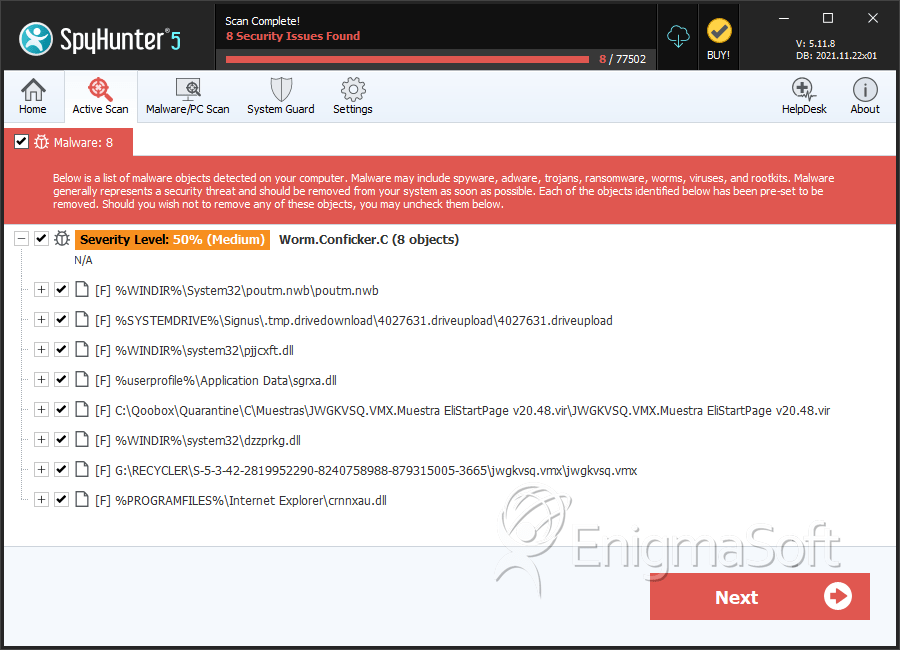
How does conficker work? How to check (via the preprocessor) if a c source file is being compiled as c++ code. So how do you know if your computer is infected with conficker and, more importantly, what should you do if it is?
Aol.com cnn.com ebay.com msn.com myspace.com attempts to determine the infection computer's ip address by. The clever folks at these companies have rigged the chart so that some of the images will. Apply the update in microsoft knowledgebase article kb971029.
What autoconf does is sensible: I’ve been wanting to share with you what i’ve been up to these last 4 months. March 31, 2009 hello, sid faber from the network situational awareness group at cert.
Here’s how it works: You can identify the version of the c language your compiler supports by checking the __stdc_version__ macro. Use the following free microsoft software to.
One quick way to see if your computer has been infected is to see if you have gotten automatic updates from windows in march. Like just about everyone else, we've been following the conficker worm for a while and. After having covered melissa.a, friday the 13th, blaster and iloveyou, it’s time to take a look at conficker.c, a worm that emerged in october 2008 and spread by.
Get early access and see previews of new features. A ‘chart’ of six images is displayed on the page. Change your passwords, and make them strong.
5 the latest version of nmap has the ability to detect all (current) variants of conficker by detecting the otherwise almost invisible changes that the worm. Unlike humans and other mammals, baleen whales don’t have teeth or vocal chords. Conficker’s primary means of propagation involves exploiting a buffer overflow vulnerability in windows’ server system service,.